One of our users recently encountered the “Your sign-in was blocked” error while attempting to access a channel on Teams that a customer had supplied. We were able to solve the problem using Azure Active Directory. So today, I’ll teach you how to fix your Microsoft 365 sign-in being restricted.
How to fix “your sign-in was blocked” error in Microsoft 365:
- First, sign in to your
 Office 365 account.
Office 365 account. - Use the
 app launcher and navigate to “Admin.”
app launcher and navigate to “Admin.” - In the admin dashboard, under “Admin centers,“ click on “Azure Active Directory“ (you may need to click “Show all“ to find the admin centers).
- Click on “All services.“
- Now click on “Azure Active Directory.“
- Click on “Security.“
- Now click on “Risky users.“
- Finally, select the user and click on “Dismiss user risk.“
For me, a sign-in error appeared due to an old dangerous sign-in attempt. Once safely dismissed, we fixed the “your sign-in was blocked” error.
We’ve also created a video to help guide you through the steps:
 |   | Empower your devs with DevSecOps Give your devs the tools they need to create & deliver secure, innovative applications quickly and collaboratively. Get expert help migrating & modernising Set up your cloud environment confidently with help from the Azure Migration & Modernisation Programme. | |
| | 30 day FREE trial |
What is Azure Active Directory and how can it fix the “your sign-in was blocked” error?
So, what is Azure AD and why does it play such a big part in Office-based tasks such as this one here where manipulation of users’ secure login can be achieved? Azure Active Directory (Azure AD) is a cloud-based identity and access management solution from Microsoft that allows your employees to sign in and access resources in the following locations:
- Microsoft 365.
- Azure portal.
- SaaS services.
- Internal resources (apps on your company’s intranet and network).
- Cloud apps built by your company.
You may use Azure AD as an IT administrator to limit access to your applications and app resources based on your business’ needs. For example, when accessing critical corporate resources, you may utilize Azure AD to enforce multi-factor authentication. You may also utilize Azure AD to automate user provisioning across your cloud apps. Finally, Azure AD provides you with sophisticated features to help you safeguard user identities and credentials while meeting your access governance needs.
Azure AD is required for sign-in and identity security in Microsoft Online business services such as Microsoft 365 and Azure. If you sign up for any Microsoft Online business service, you’ll be given access to Azure AD, including all free services.
You can upgrade to Azure Active Directory Premium P1 or Premium P2 licenses to add premium functionality to your Azure AD deployment. Azure AD subscription licenses provide self-service, better monitoring, security reporting, and secure access to your current free directory for your mobile users.

Creating a remedy policy to fix “your sign-in was blocked” error
All active risk detections go towards calculating the user risk level. The user risk level (low, medium, or high) indicates an account’s likelihood of being hacked. As an administrator, you want to ensure that any risk detections are closed so that the affected users are no longer in danger.
If you have assessed the risk detection and found it is not dangerous, you can designate it as “Closed (system).”
Administrators have the following remediation options:
- Risk policy and self-remediation
- Reset your password by hand
- Ignore the user’s risk.
- Individual danger detections should be manually closed.
Risk policy and self-remediation
Users who have self-remediation enabled in their risk policies, such as Azure AD Multi-Factor Authentication (MFA) and self-service password reset (SSPR), can unblock themselves when risk is discovered. To utilize when risk is recognized, users must have already enrolled for Azure AD MFA and SSPR. After then, the detections are regarded as complete.
Although certain detections may not elevate risk to the point where user self-remediation is necessary, administrators should assess them anyway. Additional safeguards, such as banning access from certain areas or decreasing the acceptable risk in regulations, may be required by administrators.
Ignore the user’s risk
You can choose to reject user risk detections if a password reset is not an option for you, such as if the user has been erased.
All events are closed, and the affected user is no longer at risk when you click “Dismiss user risk.” However, because this approach does not affect the existing password, it does not restore the connected identity’s security.
How to fix “your sign-in was blocked” error in Microsoft 365
Step by step breakdown:
- First sign in to your
 Office 365 account.
Office 365 account.
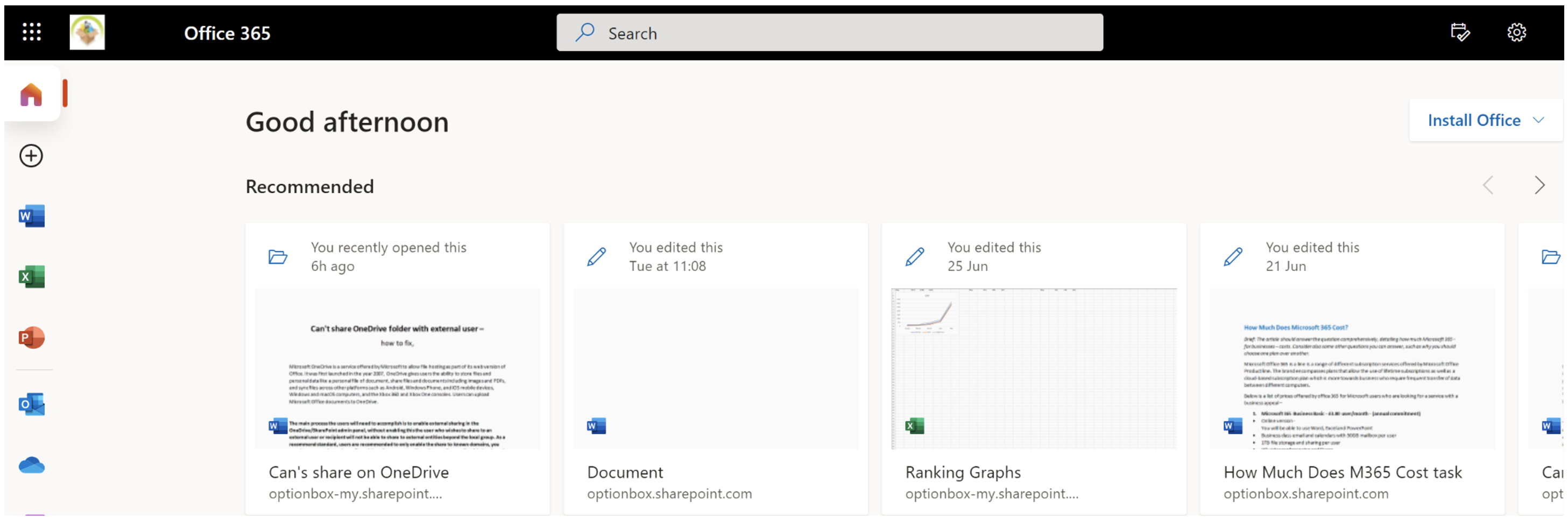
- Use the application launcher to navigate towards “Admin”.

- In the admin dashboard, under “admin center”, click on “Azure Active Directory”(you may need to click “Show all” to access).
Although “Azure Active Directory” was pinned to the menu bar in this example, you may need to choose “display all” on your dashboard to access the Azure Active Directory panel.
- Click on “All services”.
- Now click on “Azure Active Directory”.
- Click on “Security”.
- Now click on “Risky users”.
- Finally, select the user and click on “Dismiss user risk”

How this remedy will fix the error, “your sign-in was blocked”
As shown in the risk user assessment panel, there was a sign-in attempt issue caused by an old unaddressed risky sign-in event noted for the user account, which I ignored. The registration for the MFA is yet incomplete. Once safely dismissed, you’ll be able to resolve the “your sign-in was blocked” error.
Mitigating those sign-in issues caused by the risky sign-ins will help you to sign in to your account and help fix the persistent error.
Conclusion
That’s it for this Blog. Thank you for taking the time to read our content. Please feel free to email our team about how it went, if you followed the steps or if you need more help with the questions we answered in this Blog.