MFA or Multi-Factor Authentication for Office 365 is Microsoft’s own form of multi-step login to access a service or device. This stage of security allows organizations with any active subscriptions to enable multi-step security for their Office 365 users without requiring any additional purchase or subscription or plans.
Step by step process –
- To make necessary changes to the MFA of an account or group of accounts you need to first login to Office 365 which is where the admin dashboard is located to make changes possible.
- Below is the app launcher panel where the features such as Microsoft apps are located. You need to locate a feature which says admin. Click the launcher icon followed by admin to access the next stage.
- Once this is complete you will have access to the admin dashboard where you can control the entire Microsoft suite related to the organisation.
- Click show all in the navigation panel to show all the necessary details related to the changes that are required.
- After that in the list of options click on Azure Active Directory.
- Now you need to locate the Azure Active Directory, here you can make the necessary changes related to the login.
- Once this is complete you now need to scroll down the navigation panel and find the tab “company branding”
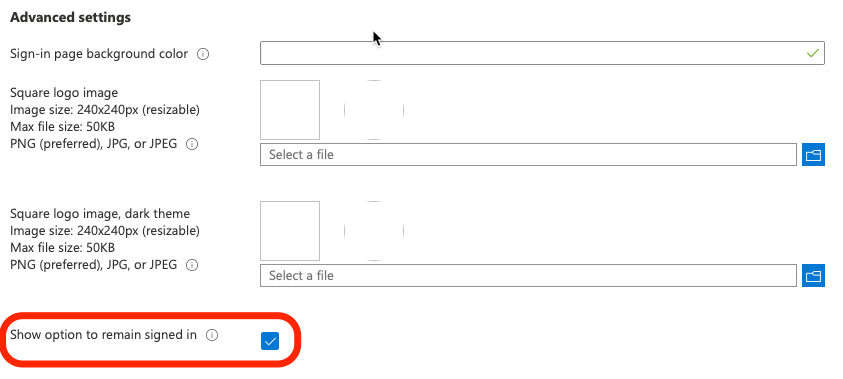
- Once this is complete a panel on the right will open up, you now need to go to the bottom of the panel (which may require scrolling down to find) and click Show option to remain signed in
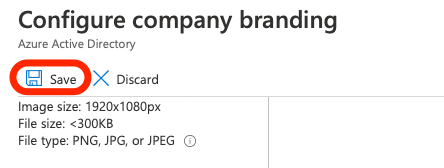
- Finally, click on save to adjust the final settings and make it active for the next time you wish to login.
MFA will greatly improve the security of users logging in to cloud services and is more robust than simple passwords. With Office 365’s multi-factor authentication, users need to confirm the call, text message, or application notification on their smartphone after entering the correct password. The user can log in only after the second authentication factor is met.
Since June 2013, Office 365 management roles can use multi-factor authentication, and today they have had the ability to extend this feature to any Office 365 user. Microsoft has also enhanced the features that have been available since June. The company is adding application passwords for users so that they can authenticate from the Office desktop application, as these have not been updated to enable multi-factor authentication. Conveniently they also allow users who authenticate from the “federated local directory” to enable multi-factor authentication. However some may choose to verify their devices and actively prevent MFA from prompting every time upon login.
After successful authentication, you will receive an access token and a refresh token to be able to access Office 365 services. The access token is only valid for one hour. This token can be either a passcode sent via SMS or can be an email or phone call to a verified email address or phone number. Once verified, you may not be asked for multi-factor authentication again for up to 90 days in Outlook or Office 365.
Below is a list of factors that could potentially cause Office 365 to prompt for MFA:
- If you sign in and out again in Office clients.
- Device inactivity for greater than 14 days.
- Recent Password changes after authentication.
- Administrators of the Office plan can apply conditional policies to restrict the resource the user is trying to access.
- Switches made between different accounts.

Azure Active Directory – Control MFA
The Microsoft agent software in charge of maintaining the MFA and user credentials and details is called Azure Active directory. Azure ensures people who are on-site or remote, seamless access to all their apps so that they can stay productive from anywhere. Other potential benefits include having the ability to automate workflows for user lifecycle.
 |   | Empower your devs with DevSecOps Give your devs the tools they need to create & deliver secure, innovative applications quickly and collaboratively. Get expert help migrating & modernising Set up your cloud environment confidently with help from the Azure Migration & Modernisation Programme. | |
| | 30 day FREE trial |
However, one of the unique factors include the ability to safeguard user credentials by enforcing strong authentication and conditional access policies. This allows users to efficiently manage identities by ensuring that the right people have the right access to the right resources which include the MFA access. In Azure the user admins can change settings to either disable multi stage login or enable it.
How to actively change MFA settings
- To make necessary changes to the MFA of an account or group of accounts you need to first login to Office 365 which is where the admin dashboard is located to make changes possible.
- Below is the app launcher panel where the features such as Microsoft apps are located. You need to locate a feature which says admin. Click the launcher icon followed by admin to access the next stage.

- Once this is complete you will have access to the admin dashboard where you can control the entire Microsoft suite related to the organisation.
- Click show all in the navigation panel to show all the necessary details related to the changes that are required.
- After that in the list of options click on Azure Active Directory.
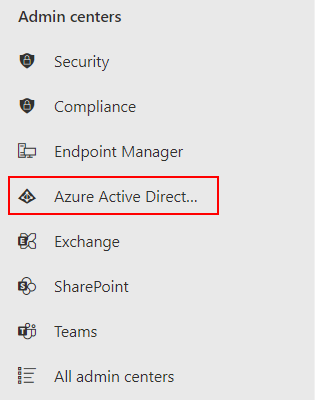
- Now you need to locate the Azure Active Directory, here you can make the necessary changes related to the login.

- Once this is complete you now need to scroll down the navigation panel and find the tab “company branding”
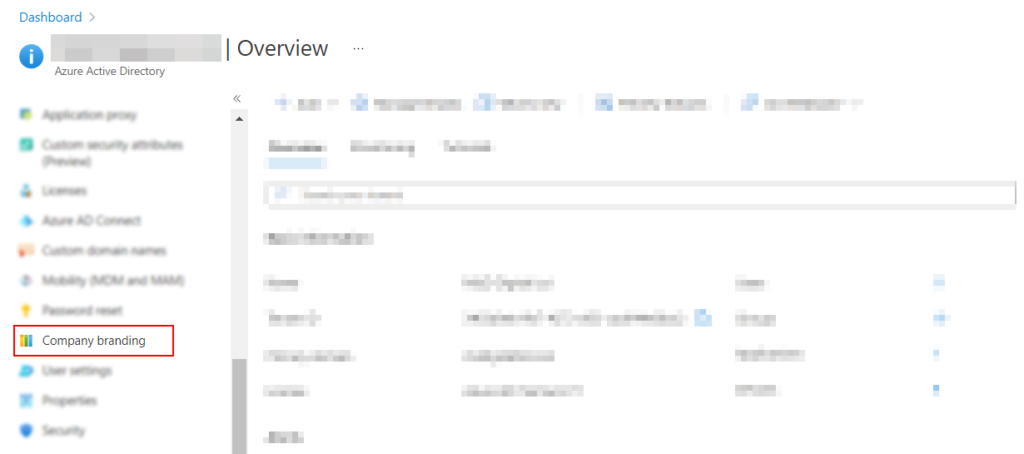
- Once this is complete a panel on the right will open up, you now need to go to the bottom of the panel (which may require scrolling down to find) and click Show option to remain signed in.
- Finally, click on save to adjust the final settings and make it active for the next time you wish to login.
The Azure AD sign-in process provides users with the option to stay signed in before explicitly signing out. This does not change the Azure AD session lifetime but allows the session to remain active when the user closes and reopens the browser. Set this to “No” to hide this option from your users.
The login frequency allows the administrator to select the login frequency for the first and second factors that apply to both the client and the user. Admins are recommended to use these settings as well as managed devices in situations where there is a need to restrict authentication sessions (such as business-critical applications).
Persistent browser sessions allow users to stay logged in after closing and reopening the browser window. Like keeping login settings, it sets a persistent cookie on the browser.
Thanks for reading! We hope you’ve found this blog post useful. If you have any other questions, please leave a comment below.