Azure Active Directory (Azure AD) is an identity and access management service that is hosted in the cloud. This service enables your staff to access external resources such as Microsoft 365, the Azure portal, and tens of thousands of additional apps. They can also use Azure AD to access internal resources. You can also enable or disable devices in Azure AD, however, what happens if you remove a device, do they still have some form of access, or do they completely lose access on their devices? Follow through for more information on what happens if you disable a device in Azure AD.
When you deactivate a device, it prevents that device from properly authenticating with Azure AD. As a result, the device would be unable to access resources that are ordinarily protected by Azure’s conditional access policy.
- What does disabling or deleting a device in Azure AD do?
- How long does it take for changes to apply when a device is disabled in Azure AD?
Above are some of the key areas you need to know about when you try to disable a device in Azure AD. If you ever come across a situation where you have disabled a device then it helps to know this information as you will be more aware of the devices that were formally added o to Azure AD.
What does disabling or deleting a device in Azure AD do?
Firstly, let’s see what exactly happens when you disable or delete a device in Azure AD. When you disable a device in Azure AD, users get access removed from their account, they won’t have any authorized access to any resources mandated and protected by Azure AD device management. When you find your device cannot access Office or any piece of network-based software, chances are that Azure AD is disabled for your device and you can’t access those resources.
Normally, when you sign in to Office 365 on an authorized device, you will be presented with this error, this will be in place of the account dashboard and again will prevent access into your account. You will also access removed to the Office suite if it’s marked on Azure. If you have a device that should remain enabled but it isn’t, follow the steps below to see how you can enable a disabled device onto Azure AD.
In-depth step-by-step guide[with screenshots] – How to enable a disabled device in Azure AD?
- Firstly, open Office 365.
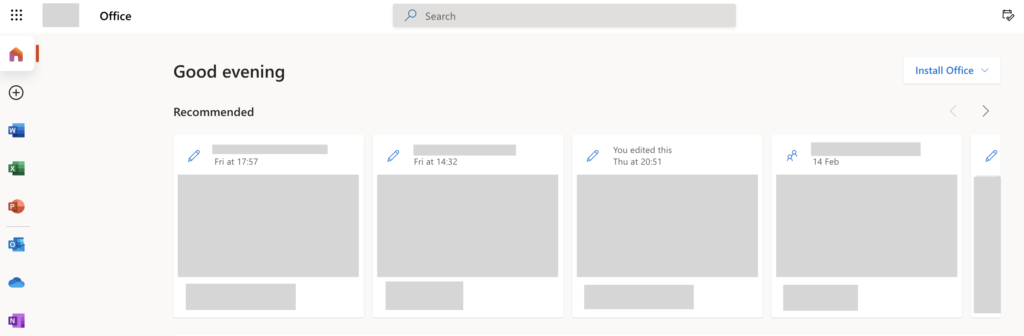
To sign in to Office 365 use your normal login details, which you would use for programs such as Outlook. When you log in you will be able to access the Office 365 dashboard where you can proceed with the steps below. The dashboard as shown above is home to all your Office based programs, resources, and content.
- Now click on the launchpad, followed by “Admin”.
The Launchpad is illustrated by nine dots in the left corner of the dashboard, click on it to display the launchpad, once you have deployed it, click on “Admin”, this will take you to the Office 365 admin dashboard.
- Under “Admin centers”, click on “Azure Active Directory”.

From there click on “Azure Active Directory”, this is under the admin center panel on the left, however, if it’s not there then simply click on “Show all”, this will deploy a collapsible menu from there you can access the “Azure Active Directory” panel.
- Click on “All services”.
- Now click on “Azure Active Directory”.
- Then click on “Devices”.

- Select “All devices”.
- From there find and select the disabled device.

- Then click on “enable”.

That’s it, once the steps above have been implemented, you will have now enabled the device and it will now have access granted on the platform and all the secured network resources will be available to that user. As an admin user make sure you verify the drive will be used in company-related tasks and won’t be used to breach data, this again falls to whether they require access or not. If they don’t require access, for instance, a new device has been issued to that user then you can restrict access to prevent a breach of data if that original device goes missing.

How long does it take for changes to apply when a device is disabled in Azure AD?
From the moment a device on Azure has been disabled, changes will begin to apply to that user’s device. It can take up to 2 hours to fully disable the user, this mainly revolves around the verification process of removing the user and the number of authorized Azure inputs that need to be disabled by Microsoft. If a device has logged out they can log back into those resources within the next 5 minutes on average. After this time frame, they will be presented with this error shown below which indicates they no longer have access to that account anymore.
However, if the user is still logged into an account they still have access to the resources for up to one hour before the restrictions disable their entire resource log. So in theory they could potentially have enough time to breach data and cause issues by leaking sensitive documents for malicious reasons.
This is why you should have MFA enabled, this will allow security prompts when a change happens to an account made by an admin user. If the MFA is enabled then the user will need to verify details, now not possible as the account has been disabled. This is effective if you want to protect preexisting resources on your account.
Conclusion
Thank you for reading our resources; please contact our team to let us know how you found the content and if you have any more questions about the issues covered in this blog. If the problems remain after you’ve tried the procedures above, please contact our experienced team at any time, and we’ll help you resolve the recurring error that’s causing problems in your business. Please let our team know by leaving a comment, and we’ll take care of it. Others who are experiencing similar issues will be able to find answers as well.
